New Section: PoC Week
TL;DR: there’s a new website section here that reviews the week’s most mentioned CVEs with public PoCs
elon killed the cvetrends star
cvetrends.com was an amazing offsec resource.
It gave you a dashboard of all the most relevant vulnerabilities based on what was trending on infosec twitter. I used to have it on as a 3rd screen throughout my workday and it was indispensable. Here’s the UI:
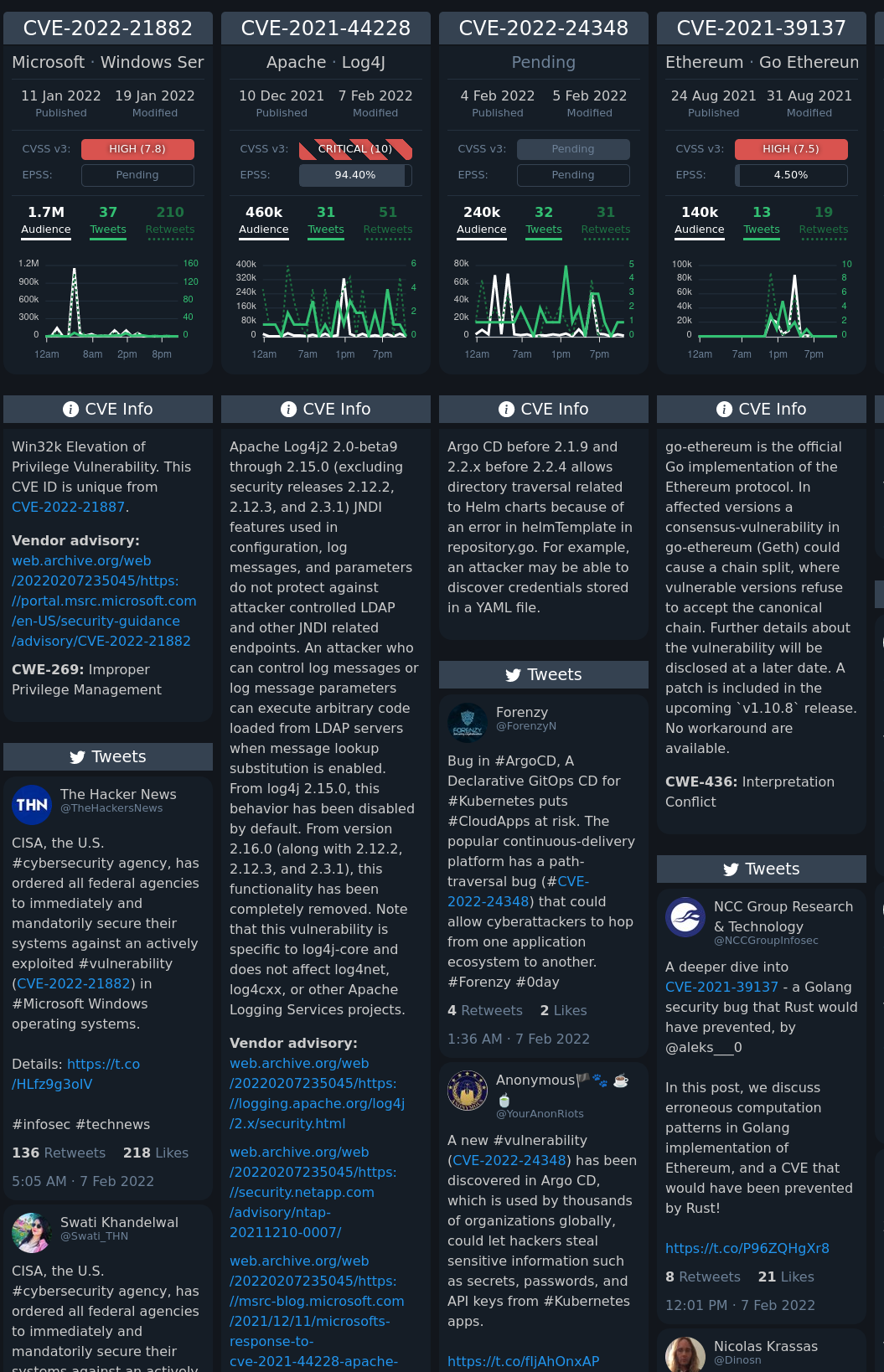
Beautiful.
Then twitter started charging for data scraping and the developer had to shut it down. A huge shame, I’d personally happily pay a monthly fee for the info.
Anyway, when it shut down my third screen changed to twitter on refresh. Which was pretty useful at first as the people I follow post excellent stuff. Then the algorithm changed and there was an increasing amount of absurd ragebait in there so it became less than useless for offsec work (and a fun-house mirror of the most virulent societal trends today, but that’s another matter).
the void
This was over a year ago and since then I’ve been looking for a place to get concise info on the most relevant CVEs from an offensive standpoint. That is, the vulns that most organisations should be prioritising - which usually means public PoCs.
There are loads of great newsletters but reading them all takes an age and to stay updated as a tester, I need to know relatively little:
- what are the most important CVEs at the moment?
- how do they work?
- how do you detect and confirm (i.e. exploit) them?
- how do you remediate them?
I’m still not aware of any one resource that gives you just this information in the elegant way that CVETrends did (if you know one, please get in touch) so I decided to hack something together myself.
the workaround
This is where the new website section PoC Week comes in!
Scraping reddit, twitter etc. was out of the question as the APIs are monetised, so I decided to scrape my own mail inbox.
PoC Week takes all the (best) security newsletters of the last 7 days, ranks the CVEs by mention count, and lists them. But it only lists those with public PoCs - i.e. vulns that you can go out and (legally) detect, confirm and mitigate right now.
It’ll never fill the void of CVETrends, but it’ll be useful for me at least. I foresee a lot of repetition as trends change slowly, but hopefully it’ll be a good place to quickly get an overview of the offsec landscape each week.
Thanks for reading, let me know what you think by getting in touch.